Verify JWT Token
When the HTTP Bearer authentication scheme is applied to a RESTHost svc operation, the verification of incoming JWT tokens is implicitly handled by Linx during the security validations . This means to say, that you do not have to create additional logic to verify the token as this verification is handled based on the shared secret key configured Auth config.
Once the security validation event has succeeded, data relating the the authentication event is passed through to the operation via the $.Input.Data.HTTPContext.User
For the HTTP Bearer security scheme, the unique_name claim value is extracted from the JWT Token and then passed in through the Data.HttpContext.User.name value. This way, the unique_name of the token can be passed through to your operation without having to re-extract this information which can be used to lookup token specific resources in the operation.
However, only this unique_name claim is extracted from the JWT token and not the rest of the payload which contains other pieces of information (claims) you may want to use. In order to extract this information, you need to explicitly verify the token in Linx.
In order to verify the entire payload, the Authorization header containing the token value must first be extracted from the request.
This value can then be verified using Linx functions.
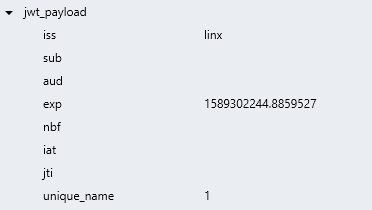
The result of this verification will be:
Verified: Y\N TYP value to indicate if the token is validPayload: AJSONformatted STR TYP containing the token'sclaims.
Once you've deserialized the payload into the Custom TYP you used to generate the JWT token , you are able to use the necessary information that was contained within it.
Parsing Headers
In order extract the payload from the token, in whichever event or operation, you need to parse the HTTP Context for the Authorization header.
"Headers": [
{
"Key":"Authorization",
"Value":[
"Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpc3MiOiJsaW54Iiwic3ViIjoiIiwiYXVkIjoiIiwiZXhwIjoiMTU4OTI4MjcwMC4wMDA2NzYyIiwibmJmIjoiIiwiaWF0IjoiIiwianRpIjoiIiwidW5pcXVlX25hbWUiOiIxIn0.LsZlMZ7ST7aqVOknQVymF9Idd-rnKE7rrVZP6_OQEOk"
]
}
]
You can achieve the result by using a single Linx expression (below) involving linq operators.
= $.Input.httpsContext.Headers.SelectMany(headers => headers.Value).Where(item => item.StartsWith("Bearer ")).First().Replace("Bearer ","")
Expression breakdown:
$.Input.Data.HttpContext.Headers: Returns all headers.SelectMany(headers => headers.Value): Returns all the items contained in theHeader.Valuelists of all headers as once..Where(item => item.StartsWith("Bearer ")): Filter items for the string "Bearer ", returns a list of items matching the filter..First(): returns first item in the list..Replace("Bearer ",""): Replaces the text"Bearer " with empty text resulting in thebase64encoded credentials.
The above expression logic will result in the JWT token string submitted in the Authorization header.
Extract Payload
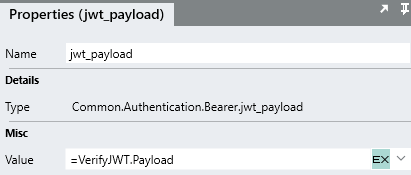
In order to extract the payload from the JWT token string, use VerifyJWT FNC.
The VerifyJWT FNC has the following Properties:
- Secret key: Signing key used to generate the token .
- Token: will be the STR TYP that was extracted in the previous step.
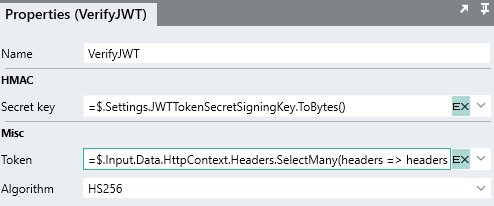
The result of VerifyJWT FNC will be like below:
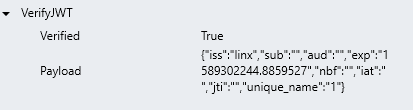
The Payload result, can then be assigned to the jwt_token TYP that was created when generating the tokens or you can import the Payload as a new Custom TYP and then assign its value as either directly in the process Function or as an Output of the process Function